

Snow College Computer Information Systems provides an engaging learning environment that prepares students for employment in the computer networking field through current, rigorous, and hands-on learning activities. Computer Information Systems covers a broad range of career opportunities. Companies large and small need employees skilled in CIS-related specialties, resulting in extensive options for a successful career.
The beauty of computer information systems is that you can choose your specialty in a demanding career field where there are ample career opportunities to choose from.
If you enjoy computers, are interested in the inner workings of a network, and would like to learn how to protect a network from cyberattacks, a career in Computer Networking and Cybersecurity is for you. These fields are fast-paced and always evolving. To be successful, you don’t just need to learn the current technologies, you need the skills to help you stay current. Our professors are not only trained and certified, but they also have real-world experience in the networking and cybersecurity industry. That means you’ll be taught by professionals who know what it takes to succeed!
Apply Now
One Semester
Certificate of Proficiency
Networking

One Semester
Certificate of Proficiency
Networking & Cybersecurity

One Semester
Certificate of Proficiency
Advanced Networking & Cybersecurity

2 years (69-71 credits)
Associate of Applied Science

Tuition*
$1360-$5525, $85 per credit
Student Fees
$192 per semester
* Tuition and fees are subject to change.

Tools
$100 (approximate)

Books
$397 per year (approximate)

Fall

Spring
Students may start this program at the beginning of fall or spring semester. (August, January)

31% Growth
Job Outlook

$82,050
Network Administrator Average Salary
$88,748
System Analyst Average Salary
$71,090
Network Engineer Average Salary

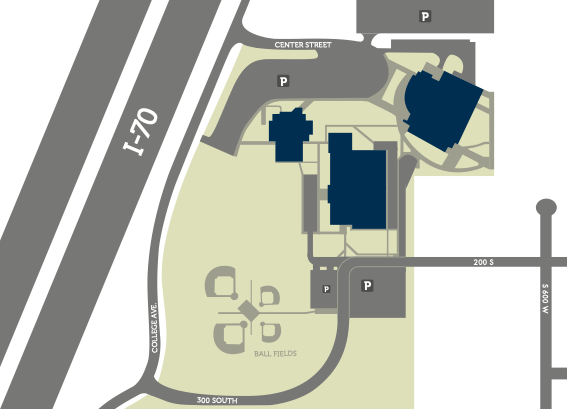
Richfield Campus

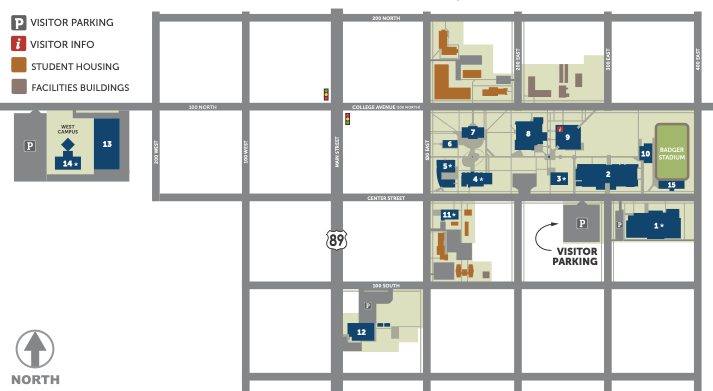
Ephraim Campus
| Course # | Title | Credits |
|---|---|---|
| CIS 1000 | CIS Orientation | 1 |
| CIS 1125 | IT Essentials | 4 |
| CIS 1130 | Networking Basics | 3 |
| CIS 1140 | Network Essentials | 4 |
| CUS 1310 | Network Security Fundamentals | 4 |
| CIS 1200 | Introduction to Networks | 3 |
| CIS 1205 | Switching, Routing, and Wireless Essentials | 3 |
| CIS 1415 | Cloud Essentials | 3 |
| CIS 1500 | Information Security Fundamentals | 3 |
| CIS 1620 | Linux Fundamentals | 4 |
| CIS 2200 | Scaling Networks in the Enterprise | 3 |
| CIS 2205 | Wide Area Networking Fundamentals | 3 |
| CIS 2310 | Security Essentials | 3 |
| CIS 2320 | Penetration Testing Fundamentals | 4 |
| CIS 2410 | Cyber Security System Analyst | 4 |
| Subtotal | 49 | |
| The above courses will earn you a Technical Education Certificate in Networking and Cybersecurity | 49 | |
| MATH 1050 or AT 1715 | College Algebra or Applied Technical Math | 3-4 |
| ENGL 1010 or BUS 2200 | Expository Composition or Business Communication | 3 |
| GNST 1200 or BUS 1170 | Foundations or Human Relations in Organizations | 3 |
| BUS 1020 | Computer Technology and Applications | 3 |
| Subtotal | 9-10 | |
| BUS 1600 | Entrepreneurship Seminars | 1 |
| BUS 2010 | Business Computer Proficiency | 43 |
| BUS 2200 | Business Communications (can't be counted twice) | 3 |
| BUS 2222 | Entrepreneurship | 3 |
| BUS 2650 | Management Principles for Entrepreneurs | 3 |
| Total Credits for AAS | 63-65 |
| Course # | Title | Credits |
|---|---|---|
| CIS 1000 | CIS Orientation | 1 |
| CIS 1125 | IT Essentials | 4 |
| CIS 1130 | Networking Basics | 3 |
| CIS 1140 | Networking Essentials | 4 |
| CIS 1310 | Network Security Fundamentals | 4 |
| Total Credits for Certificate | 16 |
| Course # | Title | Credits |
|---|---|---|
| CIS 1200 | Introduction to Networks | 3 |
| CIS 1205 | Switching, Routing, and Wireless Essentials | 3 |
| CIS 1415 | Cloud Essentials | 3 |
| CIS 1500 | Information Security Fundamentals | 3 |
| CIS 1620 | Linux Fundamentals | 4 |
| Total Credits for Certificate | 16 |
| Course # | Title | Credits |
|---|---|---|
| CIS 2200 | Scaling Networks in the Enterprise | 3 |
| CIS 2205 | Wide Area Networking Fundamentals | 3 |
| CIS 2310 | Security Essentials | 3 |
| CIS 2320 | Penetration Testing Fundamentals | 4 |
| CIS 2410 | Cyber Security System Analyst | 4 |
| Total Credits for Certificate | 17 |